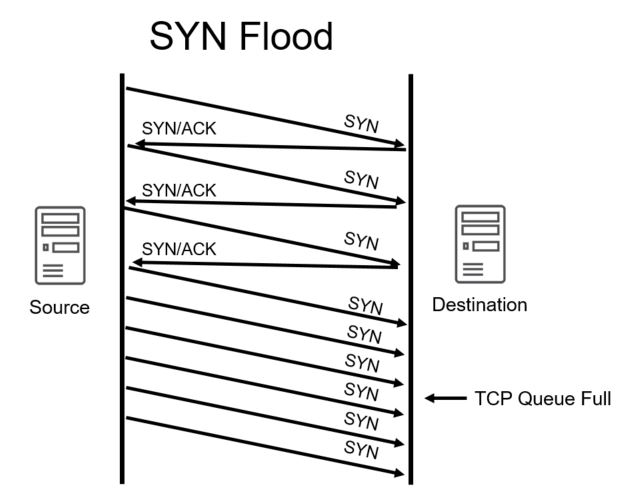
If you are being hit by a SYN FLOOD attack you can mitigate it by doing the following.
1. Disable conntrack for SYN packets (note: example below is untested, general idea should be right)
`iptables -t raw -A PREROUTING -p tcp –tcp-flags SYN -j NOTRACK`
2. Enable SYN cookies
`net.ipv4.tcp_syncookies = 1` in sysctl.conf.
I wouldn’t bother trying to use tricks like blocking specific IP’s or ranges; or applying limits per IP (e.g. using the iptables hashlimit module) as most of the time syn floods are spoofed.